A virtual private network (VPN) is set up using a tunneling protocol, which is typically layered and encrypted. To establish the VPN connection, it is necessary to authenticate both tunnel endpoints. This is a crucial step to ensure the privacy and security of the connection, which encrypt the traffic and mask the IP address.

This authentication process can be done using a number of different cryptographic methods: password, two-factor authentication, biometrics, etc. One of the most secure and resilient way of authenticating the tunnel endpoints is to use a digital or public key certificate. This authentication method is especially common in network-to-network tunnel connections.
So why is it better than other encryption methods such as symmetric cryptography (using a private key) and asymmetric cryptography (using both a private key and public key)? The answer is simple: to ensure the security of both these methods, one needs to make sure that the private key always remain a secret. A private key is therefore a major source of vulnerability. And what about a public key, how does any given party ensure its integrity? To resolve these issues, Certificate Authorities (CA) were introduced.
What is a Certificate Authority (CA)?
A CA is simply the issuer of the digital certificates. They are an essential part of the Public Key Infrastructure (PKI), which manages the public-key encryptions and the digital certificates. A PKI associates each public key with its owner’s identity using a registration process (carried out by the Registration Authority) and a certificate issuance process (carried out by the CA). The CA certificate is an electronic file which serves to attest the ownership of a given public key.
CAs issue and help manage the combination of public and private keys, thus ensuring the integrity and confidentially of the keys within the PKI. PKIs and CAs were introduced as a third-party entity whose role is to ensure that public keys are genuine, authentic and uncompromised. CAs enable anyone to verify the ownership of a public key. They are a powerful way to counter so-called “man-in-the-middle” attacks.
CAs will typically charge people or organization who want to issue a certificate. While they are recognized as the most secure and resilient authentication method today, it can be burdensome and expensive to rely on them for authentication, as compared to simpler pre-shared secret keys. But are CAs truly secure and can we trust them?
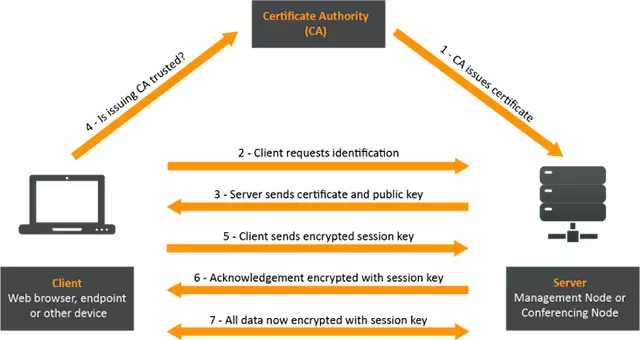
CAs were designed to be a third-party, separate mechanism within the PKI that issues the certificates. The fact that CAs are built to be independent from the PKI and be the only party that can issue the certificates is what makes them trustworthy. The PKI as a whole manages the encryption of these certificate while the CA manages authentication, aka identity verification. This separation is vital to trusting a CA, otherwise any actor could issue and authenticate its own keys.
The way they were designed, CAs are never in possession of the certificate’s private key it signs. And that is why we trust them: it is impossible for them to intercept any communication that relies on their work. There is no backdoor.
However CAs are not completely void of vulnerabilities and have been hacked before. Recent examples include the hacking of COMODO CA and the TurkTrust Inc CA which resulted in them issuing fraudulent certificates. The hackers are usually state-sponsored because of the complexity to carry out such a hack. The most striking example is DigiNotar, which was allegedly hacked by the Iranian government in 2011. The hackers subsequently issued fraudulent certificates which they used in man-in-the-middle attacks.
This does not mean we shouldn’t trust CAs or that they are insecure. No IT tool is void of vulnerabilities CAs implemented within a PKI remain the preferred way of securing the transfer of information. CAs were never designed to be the final answer that makes the whole web safe. Rather, they are one of many tools in a complex system that help make the web more secure. Their role is to help independently verify identities online. The web can only be secure if other solutions are implemented, starting with web browsers, which actually verify said certificate and come with CA trust lists.
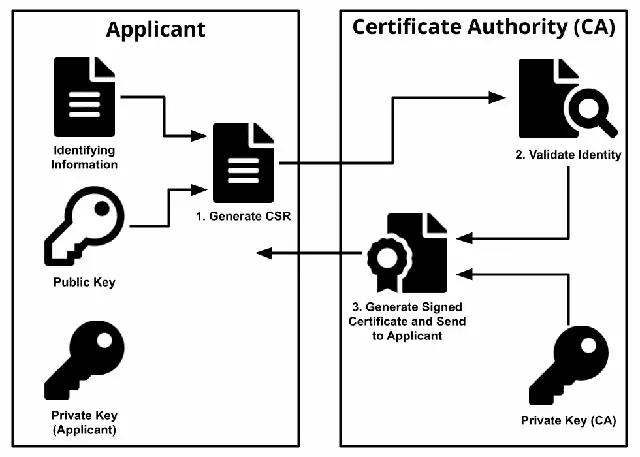
What is a HTTPS certificate?
One of the most common use of CAs is Secure Sockets Layer (SSL) certificates, which are certificates that are signed using HTTPS (“S” stands for “Secure”), the well-known web securing browsing protocol. They can be installed on any web server that wants to initiate a secure connection to a browser or another server. In recent years, SSL certificate has become the first choice technology for securing and encrypting the communication of any data.
In the complex landscape of online security, comprehending the certificate lifecycle, especially the pivotal role of Certificate Authority (CA) certificates, is crucial. These certificates play a fundamental role in establishing trust and encryption on the internet.
The lifecycle begins with the issuance of a CA certificate. Certificate Authorities are entities responsible for validating the authenticity of entities such as websites. They issue digital certificates, binding a public key to an individual or organizational identity. These certificates act as cryptographic keys, facilitating secure communication by encrypting data exchanged between a user’s browser and a website’s server.
Renewal is a critical aspect of the certificate lifecycle. CA certificates have a finite validity period, typically ranging from months to several years. Renewing certificates ensures continuous security and compatibility with evolving encryption standards.
Revocation, the next phase, involves invalidating a certificate before its expiration date. This may occur due to a compromised private key or changes in an organization’s status. Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) responses convey the revocation status to relying parties.
Understanding the intricacies of CA certificates and their lifecycle is imperative for maintaining a secure online environment. Regular updates, adherence to best practices, and reliance on reputable CAs contribute to a robust security infrastructure, safeguarding digital transactions and communications.
Conclusion
CAs heavily invest to ensure they have resilient infrastructure and operations in place to authenticate users and issue certificate. They also follow the guidelines and best practices as instructed by the browser community. In return, they charge a fee to any customer who wants to issue a certificate.









