When we use the Internet how we usually do, we connect our devices directly to servers via sites and mobile applications. Thus, servers recognize the IP address of the user and its location and any information that comes from that specific IP. Internet Providers access this information and use it for commercial purposes such as advertising campaigns, creating a portrait of the users’ online presence, and then selling this information to even bigger corporations. Sadly, at the end of the day, that isn’t even the biggest threat online. A much greater threat is posed by hackers who through an unsecure Internet connection can access the user’s data. If you do not use special tools to protect your data, you can easily fall victim to a hacker. The main target data of hackers are your bank card data, passwords, and any form of login credentials that can help them access personal correspondence in your mail or social media channels.
What is a proxy-server
A proxy is an intermediate server that acts as the middleman between a user and other virtual servers. This way you are provided access to websites in a much more secure way. When your data is circulated via proxy servers you can disguise your data from any harmful third parties, including internet providers which may sometimes block certain websites and their content in your specific geographical location. When browsing the web via proxy servers you are given the ability to bypass restrictions and visit sites you need that your ISP has blocked.
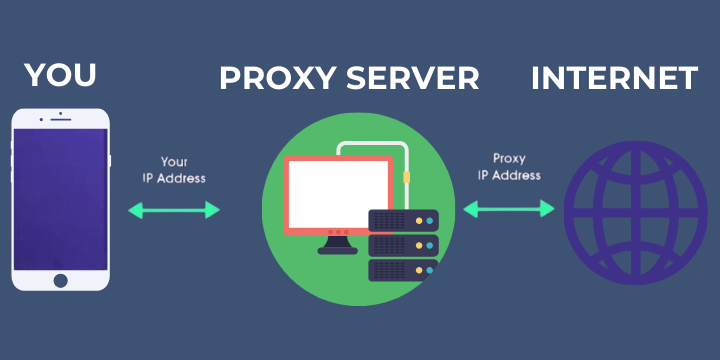
How to use a proxy server
Thanks to proxy servers we as internet users are given a chance to browse the web without anyone stalking what we browse and what personal information we enter when browsing the web. Internet providers and owners of big commercial websites will not be able to track any of your cyber movements thus, your internet identity and online data are safe.
- CachingWhen you frequently visit the same websites, copies of your webpage visits are made and stored on the proxy server. This way when you revisit any website the loading speed is reduced.
- Data compression. A virtual machine downloads data files from the Internet, and the user gets the result in a compressed form. This saves external traffic.
- Access control. The administrator can restrict access to certain resources to other users. This option also helps to filter intrusive ads and to skip viral software less.
![]()
Proxy Server Types
There are 3 main types of proxy servers: transparent, anonymous, and reverse. Below you will find a detailed breakdown of each type of server and the difference between all of them.
- Transparent Proxy
An open proxy does not change any user data. It handles all HTTP traffic and does not mask the IP address of the user. This type of proxy is most often used by system administrators in offices to restrict employees’ access to certain web resources. The biggest disadvantage of this type of proxy is the low level of data protection.
- Anonymous Proxy
An anonymous proxy changes the IP address of the user. This way it ensures the anonymity of the user’s IP address when he or she is browsing the web. This type of proxy slows down the response process in the Internet environment but at the end of the day, it does keep the user’s internet movements confidential.
- Reverse Proxy
The Reverse proxy servers extract web pages on behalf of a client from one or more VMs. The user then receives this response as if it were coming directly from a proxy server.
How to choose a proxy server
To decide on the right proxy, you should consider your wants and needs for the specified servers. Below you will find a list of things you should take into consideration when choosing a proxy server for your cyber needs.
- The Location Of The Server – The real-life location of the server plays a major role in the effectiveness of proxy servers. This way when browsing the web via that server your virtual IP address will be from the country where the proxy server is located.
- Note That Not All Proxy Servers Are Equally Useful – Restrictions may arise due to geographical restrictions of certain types of web content. For example, most free torrent services are blocked within the United States, yet, if you google them from a Ukrainian or Russian IP for example, they will be available.
- Pay Attention To The Server Ping- The higher the ping value, the slower requests to and from your proxy server will be. This will affect the speed at which web pages are loaded and the productivity of your network overall.
- It may not work. This can be checked with free online services that help you check the status of this or that proxy server. They analyze the proxy for availability, type, and country. It is possible to test individual IPv6 proxies.
Methods of ensuring security in the online environment
Besides simply using proxy servers, there are many other data protection technologies out there to ensure maximum security for your online identity. One of the most popular ones is a Virtual Private Network which is also known as simply, a VPN. Thanks to the use of data encryption and a bunch of other security measures a user can browse the web in absolute safety. Both Proxies and VPNs protect internet users from harmful third parties such as hackers and espionage software that may be present with some ISPS (Internet Service Providers). Both technologies have their strengths and weaknesses.
What is the difference between VPN and Proxy server
The main difference is that these are two different technologies. Both are aimed at solving security problems, but VPN is a virtual network and proxies are an application protocol. The working principle is also different. The VPN works on the network (channel) level: the connection is made without an intermediary. It’s safe and convenient to work via a virtual network when we connect to public Wi-Fi. When connected to a VPN your data is encrypted and none of your personal information will be compromised by harmful third parties. Thanks to a VPN not only are users protecting their data, they are also protecting their devices from any harmful virus software.
![]()
Advantages of use: proxy server and VPN
The main difference between these technologies is the degree of security that they provide in different conditions. Both VPNs and proxies can hide client IP addresses as well as personal data. But thanks to VPN the user will be able to get a set of security measures, which are not present when using proxy servers. To get a better understanding of which of the two is better to use it is necessary to take into account all of the pros and cons of both.
- Privacy Online
VPN protects personal information (such as passwords to sites and devices) from malware and hackers by encrypting all transmitted data. A proxy cannot guarantee this high level of security and is not always able to hide your movements and passwords online. Due to that specific reason, a VPN wins in the long run when it comes to cybersecurity.
- Speed of processing requests
Virtual private networks, also known as VPNs do not increase the download speed on sites. Depending on the type of data encryption and transmission protocol used, a VPN could slow down your Internet connection by up to 30%. However, if the client connects to a public network, a VPN is the most reliable tool to protect personal information. The mediating server will not necessarily affect the speed of the connection due to the lack of encryption. However, the speed of processing requests can be affected by the number of users who simultaneously use one VM.
- Security on the Internet
VPNs tend to have an algorithm for data encryption up to 256-bit. This means that the key is made up of 256 binary files and there are 2 correct combinations. This makes it extremely difficult for hackers to crack the key and access the user’s personal information. Proxies are also able to provide a form of security online, yet it will be nothing close to what a VPN can offer. The main thing is that its settings contain an option to hide the client’s IP address from websites and internet service providers. If this option does not exist, it is necessary to additionally connect a VPN to your browser to improve its security level.
What Should You Use, A VPN or Proxy?
When you visit sites from your home computer, your service provider processes a request for access rights to the web resource. It is up to you to decide if you can access some web pages. In simple words, the proxy server is a system that changes user activity in the browser, hiding the real location. A VPN connection additionally protects the connection by transmitting data in encrypted form.
Why you should consider using proxy servers:
- Filters out requests proxy servers can be used to access blocked websites and also set limitations for other users within the proxy server network.
- Data protectionIf you browse the internet directly from your original IP address, you are truly leaving your data out in the open for hackers. The security of your computer or any other device is reduced by x3-x4 times.
- Network AnonymityA proxy server may hide your actual IP address. This way the virtual machine running the target website will not be able to detect your physical location.
- Processing RequestsThanks to caching on proxy servers you will enjoy fast browsing speeds compared to VPN speeds. Proxy servers all reduce the amount of traffic coming from the targeted web service.
A VPN also offers everything a proxy server has to offer + traffic encryption of your data and a secure channel for the transmission of any outgoing data. When you are connected to a VPN you are hiding your real location and protecting all of your data from any harmful third parties.
Proxy Server vs. VPN: Making the Right Choice for Your Online Privacy and Security
In the realm of online privacy and security, both proxy servers and Virtual Private Networks (VPNs) play crucial roles, but they have distinct differences. Understanding these differences is essential for making the right choice to protect your online activities.
Proxy Server:
A proxy server acts as an intermediary between your device and the internet. When you request a webpage or resource, it forwards the request on your behalf, masking your IP address. Proxy servers are often used for:
- Anonymity: They can hide your IP address, making it harder for websites to trace your online activities back to you.
- Content Access: Proxy servers can help access region-restricted content by routing your traffic through servers in the desired location.
- Speed: They can offer faster speeds as they don’t encrypt data like VPNs, which can slow down connections.
VPN (Virtual Private Network):
A VPN creates a secure and encrypted tunnel between your device and a VPN server. This encryption ensures that your internet traffic remains private and secure. VPNs are known for:
- Enhanced Security: VPNs encrypt your data, making it extremely difficult for third parties, including hackers and ISPs, to intercept and monitor your online activities.
- Full Anonymity: They hide your IP address while also encrypting your data, offering a higher level of privacy compared to proxies.
- Protection on Public Wi-Fi: VPNs are crucial for protecting your data when using public Wi-Fi networks, preventing potential cyber threats.
Choosing between a proxy server and a VPN depends on your specific needs. If you require basic anonymity and content access, a proxy server may suffice. However, for robust security, complete privacy, and protection, a VPN is the superior choice.







